Understanding the Recent CrowdStrike Incident: A Cybersecurity Perspective
Exploring the Technical Details and Implications of the Falcon Sensor Software Failure
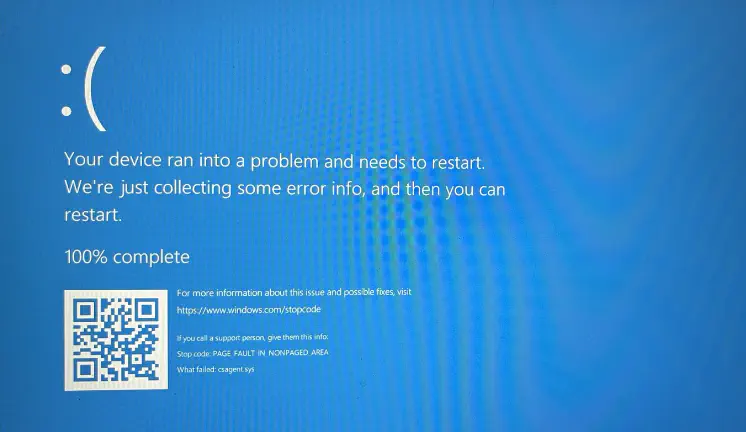 Image credit: By_Author
Image credit: By_AuthorWhat Happened?
On July 19, 2024, a significant incident involving CrowdStrike’s Falcon Sensor software caused widespread disruptions across Windows systems globally. This event, often referred to as a “Blue Screen of Death” (BSOD) incident, raised concerns within the cybersecurity community and among users reliant on Microsoft systems. Here, we delve into the technical details of the incident, the affected technologies, and the implications for cybersecurity practices.
Overview of the Incident
The issue stemmed from a faulty content update deployed by CrowdStrike, which inadvertently triggered a logic error in the Falcon Sensor software. This update, released at 04:09 UTC, was intended to enhance the software’s ability to detect and respond to malicious activities, particularly those involving named pipes—an inter-process communication mechanism in Windows. However, the update led to system crashes for many users, resulting in a BSOD and significant operational disruptions across various sectors, including airlines, banks, and cloud services like Microsoft 365 and Azure.
Technical Details
- Affected Files: The problematic file was identified as a channel file named “C-00000291*.sys.” This file is part of the behavioral protection mechanisms within the Falcon platform, designed to evaluate named pipe executions. The faulty version of this file was timestamped at 04:09 UTC, while the reverted, functional version was timestamped at 05:27 UTC on the same day.
- Impact on Systems: Systems running Falcon Sensor for Windows versions 7.11 and above that were online during the update window experienced crashes. Notably, systems running Windows 7 and Windows Server 2008 R2 were unaffected, as they do not utilize the Falcon Sensor.
- Remediation Steps: CrowdStrike quickly identified the issue and rolled back the problematic update. For users still experiencing crashes, CrowdStrike provided several workaround options, including rebooting the host to download the reverted file or manually deleting the problematic file in Safe Mode.
Technical Details and Workaround
CrowdStrike acknowledged the issue, identifying a Channel File in the update as the culprit. This file can be addressed individually, allowing users to retain the Falcon Sensor update. The company has provided the following workaround steps for affected systems:
- Boot Windows into Safe Mode or the Windows Recovery Environment.
- Navigate to the C:\Windows\System32\drivers\CrowdStrike directory.
- Locate and delete the file matching “C-00000291*.sys”.
- Boot the host normally.
Widespread Consequences
The fallout from this incident was extensive. Major airlines grounded flights, and various businesses faced operational disruptions, leading to a significant impact on global services. Social media platforms and e-commerce sites also reported service degradation, highlighting the interconnected nature of modern IT infrastructure.
Despite the chaos, CrowdStrike clarified that this was not a cyberattack but rather a software failure. The company emphasized its commitment to resolving the issue and improving its processes to prevent similar occurrences in the future. Microsoft also acknowledged the disruptions and worked to mitigate the impact on its cloud services.
Implications for Cybersecurity
This incident underscores several critical lessons for cybersecurity professionals and organizations:
- Importance of Rigorous Testing: Software updates, especially those related to security, must undergo thorough testing to prevent logic errors that can lead to system failures. The reliance on real-time updates must be balanced with the need for stability.
- Communication and Response: Organizations should have clear communication channels with their cybersecurity vendors. During incidents, timely updates and transparent communication can help mitigate panic and confusion among users.
- Backup and Recovery Plans: The ability to quickly revert to previous stable versions of software is crucial. Organizations should maintain robust backup and recovery protocols to minimize downtime during such incidents.
- Vulnerability Management: The incident highlights the potential risks associated with traditional detection methods that rely on signatures and updates. Organizations may need to explore alternative security solutions that offer more resilient protection against vulnerabilities.
Conclusion
while the CrowdStrike incident was a significant disruption, it serves as a reminder of the complexities of cybersecurity in a highly interconnected world. As organizations continue to rely on sophisticated security solutions, the importance of robust testing, clear communication, and proactive vulnerability management cannot be overstated.
References
- Crowdstrike statement on falcon content update for windows hosts
- Economictimes microsoft outage cause explained
- Crowdstrike falcon spotlight vulnerability management
- Crowdstrike technical details on todays outage
- Tomsguide-microsoft worldwide outage live
For further insights and updates on cybersecurity, stay tuned to Secure with Siva.
Note: This blog is for educational purpose only